![]()
Secure and long term authentication
(without refresh tokens)
Gabriel Zachmann, Marcus Hardt, Uros Stevanovic
EGI Conference 2021
Overview
Use Case
Long running compute job
(Longer than lifetime of Access Token)
- Load data at the beginning
- (Run computation, access other resources in between)
- Store data at the end
Goal / Requirements
- Obtain OIDC Access Tokens
- Over extended periods of time
- <=> Technical translation:
- Address security properly
- No user interaction
- Support for multiple devices (Bearer Tokens)
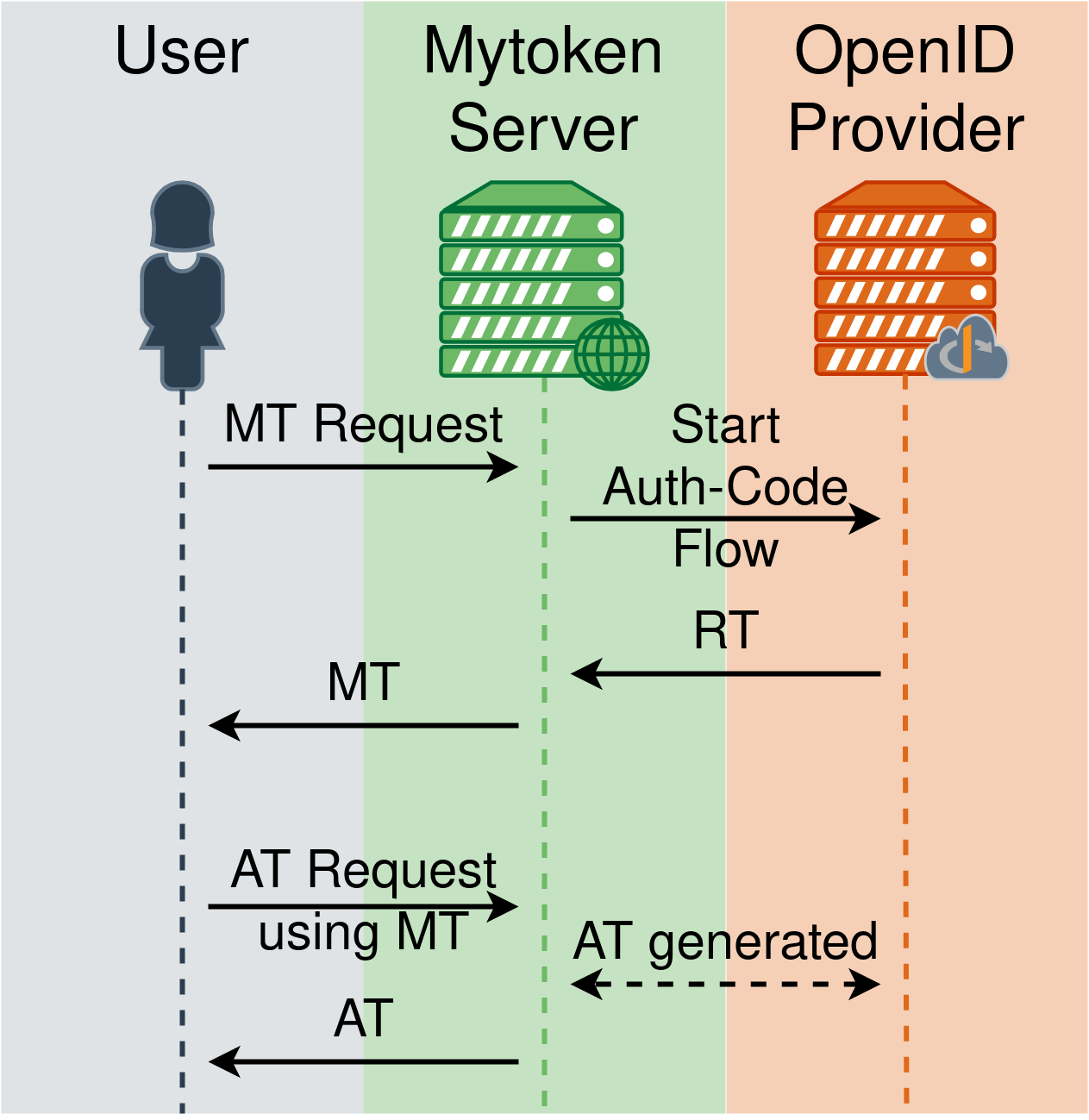
Mytoken - Concept
Basic Concept
- Mytoken Server
- Proxy for Refresh Tokens (RT)
- Implemented as an extension of OIDC
- User flow:
- Create mytoken (MT)
- Use MT to obtain
- Access Tokens (AT)
- Other mytokens
How about security?
- Mytoken allows any bearer of an MT to use a stored Refresh Token
- This is a breach in security
- Unless…
- We apply proper crypto
- We employ additional security measures
- We limit the power of mytokens
- Certainly more secure than providing the RT to the user
Creating a Mytoken
Different ways to create a mytoken:
- OIDC Authorization Code Flow
- SSH (coming soon)
- Existing Mytoken
- Create specific mytoken per use-case
- Specific capabilities
- Individual restrictions
- Create specific mytoken per use-case
Capabilities
- Examples:
- Obtain Access Token
- Create new mytoken
- List / introspect mytokens
Restrictions
- Each mytoken may be restricted (per token)
- Restrictions are flexible
- Extensible restriction dimensions
- Multiple clauses in a mytoken
Restriction
Dimensions of restrictions
- Time:
- Not before, not after point in time
- Location:
- IP address ranges
- Countries (based on geoip)
- OIDC:
scope,audience
- Number of Usages:
- Regulate retrieval of Access Tokens
- Allow / deny creation of sub-mytokens
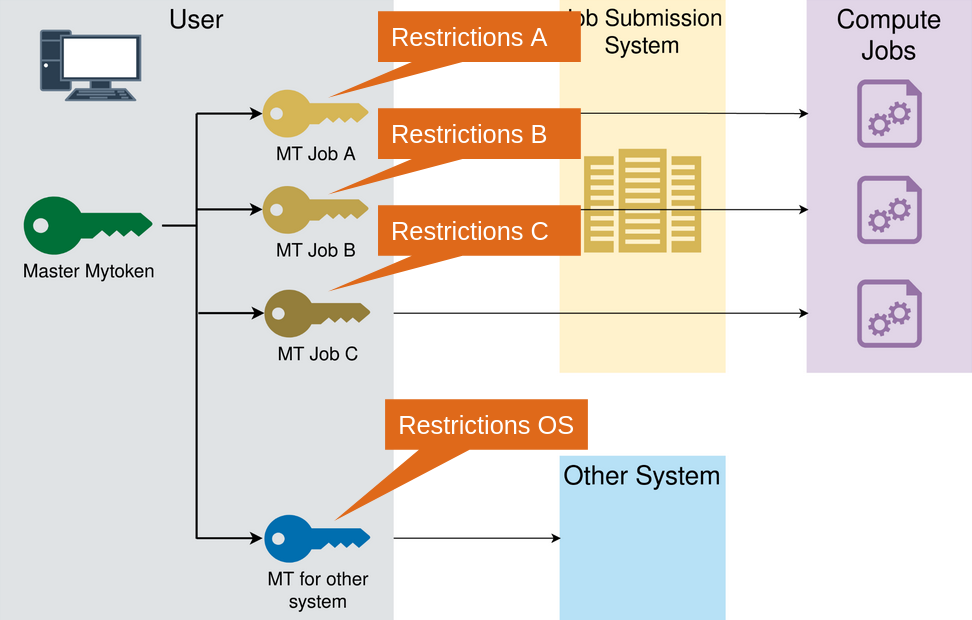
Back to the use-case
- At Job start:
- Only from Belgium Obtain AT that can
- Create computational jobs
- On Federated Cloud
- Obtain an AT that can
- Read storage
- from CERN
- Only from Belgium Obtain AT that can
No action allowed for some time - At Job end:
- Obtain AT than can
- Store the output
- at DESY
- Obtain AT than can
[{"exp" :1634300000,
"nbf" :1634400000,
"geoip_allow":["BE"],
"scope" :"compute.create",
"audience" :["fedcloud"]
},{
"exp" :1634300000,
"nbf" :1634400000,
"geoip_allow":["BE"],
"scope" :"storage.read",
"audience" :["se.cern.ch"]
},{
"exp" :1635300000,
"nbf" :1635400000,
"scope" :"storage.write",
"audience" :["dcach.desy.de"]}]Usage
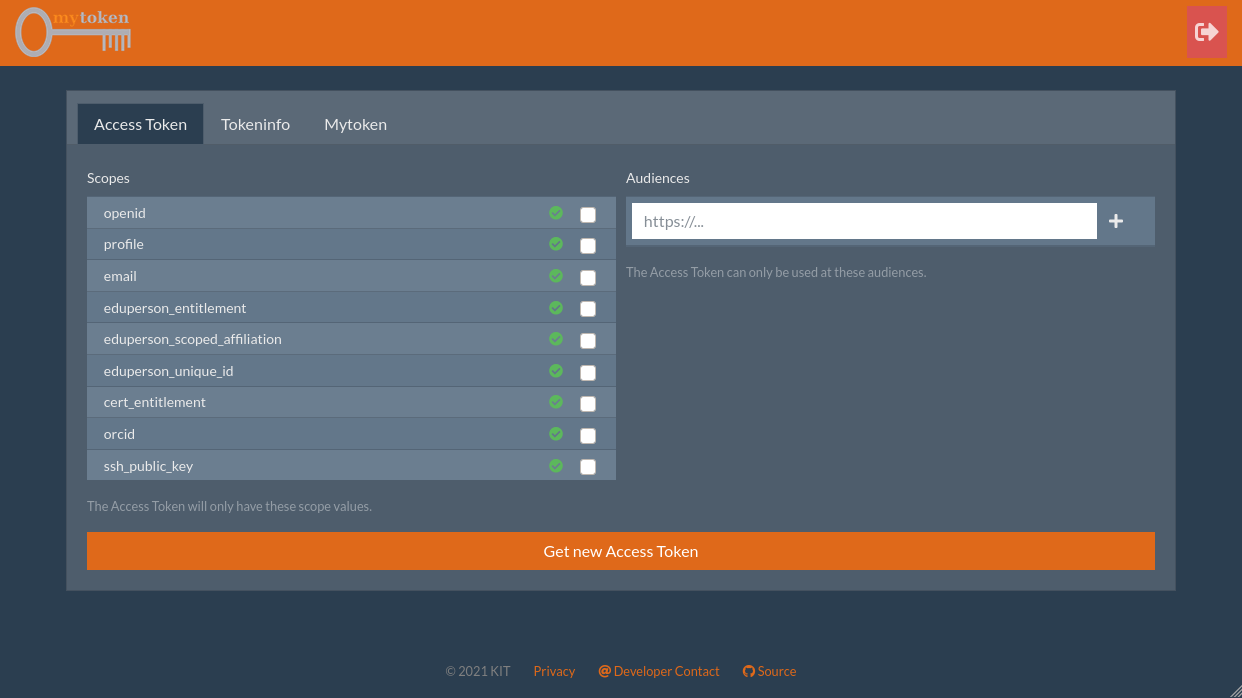
Web Interface
Command Line
No Time for Demo :(
# Create and store a mytoken under 'egi' name. Starts OIDC flow
$ mytoken MT store --oidc egi
# Create and return a mytoken from the 'egi' mytoken with restrictions
$ mytoken MT -t egi --exp=+1d --ip=this --usages-AT=5
# Obtain Access Token (using default mytoken)
$ mytoken AT
# Obtain Access Token with specific scopes and audience
$ mytoken AT -s openid -s profile -s entitlement --aud "fedcloud"Summary
mytoken - Summary
- Obtain OIDC Access Tokens from everywhere
- New service
- Restrictions allow fine-grained control over privileges